Digifortex helps in SOC II Type II Implementation and Certification globally. SOC II Type II is the System and Organization Controls (SOC2) is a framework for data protection where organisations should protect data from various vulnerabilities. AICPA (The American Institute of Certified Public Accountants) have developed the framework around 5 trust principles namely- Security, Availability, processing integrity, confidentiality and privacy. SOC2 is curated specifically for SaaS companies to meet the highest standard of data security.
Request free consultationA framework curated by AICPA, SOC 2 is based on 5 Trust Service Principles:
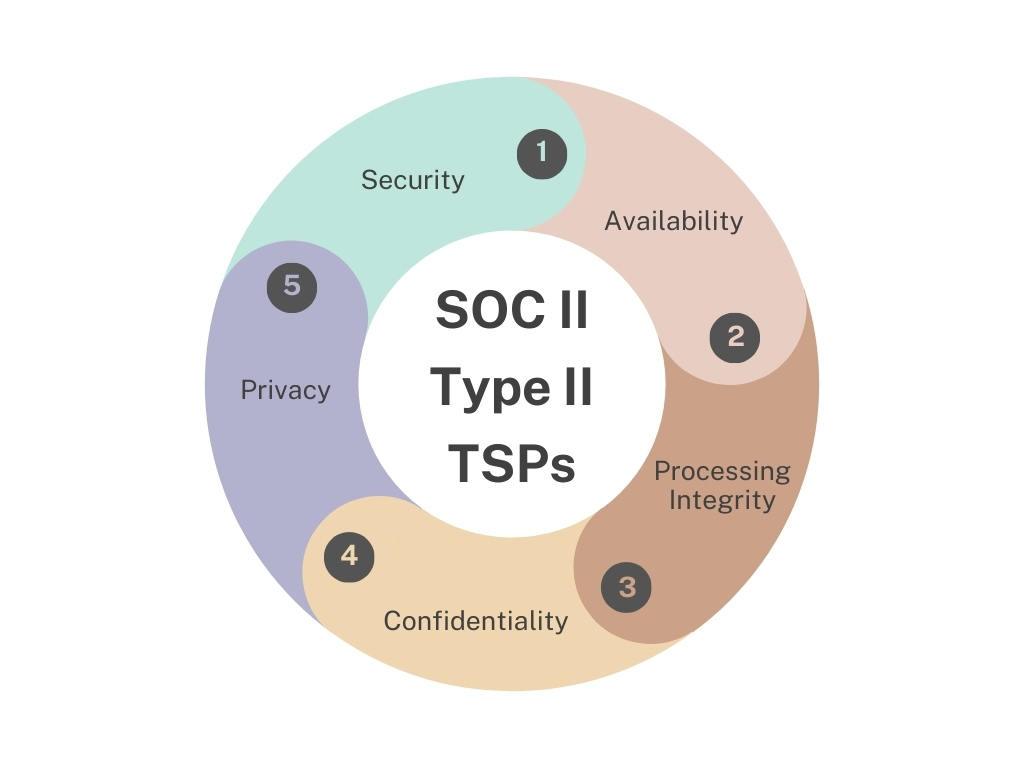
Security: Security is a fundamental infosec criteria. Security is about the measures taken to prevent unauthorised access to systems, which includes firewalls etc. It also looks out for the overall information and cyber security policies and procedures which protect the organizations systems and data from unauthorised access, destruction and modification. Service providers must have appropriate controls in place to safeguard the system.
Availability: Availability is to ensure the system is available for operation as agreed upon by the customer. Organisation should have appropriate controls to ensure availability and minimize service disruptions which includes backup, recovery procedures and disaster recovery plan.
Processing Integrity: The processing integrity principle requires service providers to ensure that the system processes data accurately, entirely and on time. Organisations should have the necessary controls to ensure data is processed accurately.
Confidentiality: Confidentiality The Confidentiality criteria looks at the protection of confidential information against unauthorised disclosure or removal. This involves identification and classification of data and applying appropriate measures based on the classification.
Privacy: The Privacy criteria, which addresses the collection, use, retention, disposal and disclosure of personal information, is based on aligning organisational operations with privacy principles and relevant legal requirements.
Contact Us to get your SOC II Type II certificate
SOC II Type II certification requires time and effort. It requires re-certification every 12 months
SOC II Type II certification cost depends and varies from one company to another. Factors which affect including company size, complexity of company’s process/procedures, location, scope etc.
DigiFortex provides consulting services to help organizations achieve and maintain compliance with the SOC II Type II. Our team of experts brings extensive experience and deep information security domain expertise (including certifications like ISO/IEC 27001 Lead Auditor, ISO 27001 Lead Implementer, CISSP, CISA and/or CRISC) ensures that all of your security policies, procedures, and practices meet the requirements set forth in the SOC 2 Trust Services Principles and Criteria.
We will also provide guidance on how to best address potential risks to data privacy and integrity so that your organization can reach its desired level of security maturity.
Project Scoping: Define the organizational and system boundaries for the assessment.
Gap Assessment: Gap Assessment compare the organization’s existing controls against with SOC 2 criteria. This helps to identify any control deficiencies or gaps that need to be addressed for compliance.
Gap Report: Gap report provides an in-depth evaluation of the organization's current practices and processes in relation to the desired standards. All the identified gaps are addressed in the report.
Gaps Closure: All identified gaps are closed by implementing the controls with in the organisation as per the standards.
Evidence Collection: It is the phase where all evidences are collected.
Evidence Review:Examines the evidence provided by the organization to validate the effectiveness of controls in place.
Evidence QA: Evidence QA ensures that the evidence provided is of high quality, enabling the auditor to make informed decisions and provide an accurate opinion on the organization's controls.
Final Assessment: CPA will conduct the final audit.
Who needs SOC II Type II? Why is it important?
SOC II Type II audits are usually conducted by organizations that provide systems and services to client organizations such as Platform as a Service, Software as a Service (SaaS), and Cloud Computing. The client company may request an assurance audit report from the service organization. The primary purpose of SOC 2 is to ensure that third-party service providers store and process client data in a secure manner.
What is SOC II Type II requirements?
Is SOC II Type II a legal requirement?
While SOC II Type II is not mandated by law, its significance and benefits in the business world where data privacy is of paramount importance is substantial.
How long will SOC II Type II implementation & certification take?
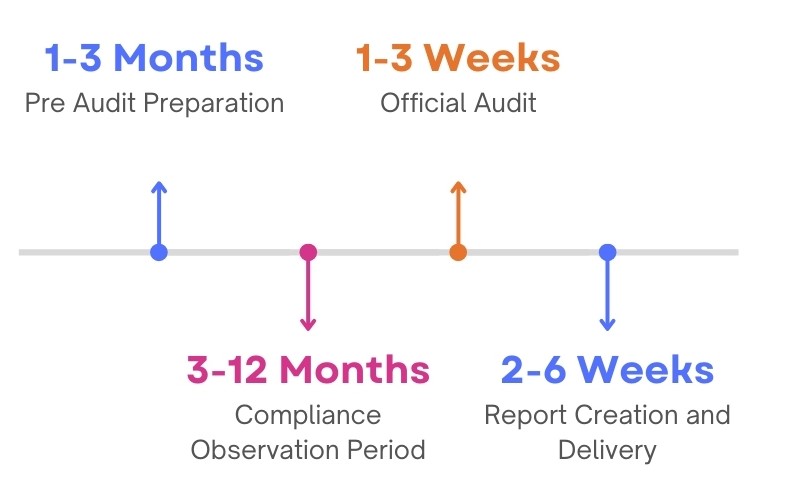
There are multiple factors which will affect the duration of audit
Typically, 3-12 months.
When does SOC II Type II certificate expire?A SOC II Type II certification is valid for 12 months from the date of issue. Companies will require recertification every year.
What is the latest version of SOC II Type II?
Trust Services Criteria – 2017 (With Revised Points of Focus – 2022)
Who provides a SOC II Type certificate?
A recognized CPA firm or an independent auditor can issue SOC 2 type II attestation.
How many stages of audits are required to be performed?
Only one i.e., CPA final Audit
How does DigiFortex helps in SOC II Type II implementation and certification?
DigiFortex assesses your current security posture and identifies areas that need improvement to meet SOC 2 Type 2 requirements. Assist in develop and implement necessary policies and procedures and implementing security controls and measures to mitigate risks and enhance security posture, ensuring compliance with SOC 2 requirements.
DigiFortex helps in documenting processes, controls, and evidence required for SOC 2 Type 2 certification, ensuring all necessary documentation is in place. DigiFortex prepares your organization for the SOC 2 Type 2 audit, including readiness assessments.