OT VAPT (Operational Technology Vulnerability Assessment and Penetration Testing)
In today's digital age, the convergence of Information Technology (IT) and Operational Technology (OT) systems has led to incredible advancements in industries worldwide. However, it also brings about new security challenges. At DigiFortex, we specialize in providing advanced OT Vulnerability Assessment and Penetration Testing (VAPT) services to help businesses secure their critical OT infrastructure against cyber threats.
Operational Technology encompasses hardware and software systems that monitor and control physical devices in industries like manufacturing, energy, transportation, and utilities. These systems are often designed to operate in isolation from traditional IT systems, making them vulnerable to modern cyber-attacks. With the rise of cyber threats, it’s crucial for businesses to proactively secure their OT environments.
Request free consultation - Click Here
What is OT VAPT?
OT (Operational Technology) refers to hardware and software systems used to monitor and control physical devices and processes in industries like manufacturing, energy, transportation, and utilities. These systems manage critical infrastructure, such as machines, sensors, and control systems.
OT PT is a process where cybersecurity experts simulate real-world cyber-attacks on OT systems to identify weaknesses. It helps organizations understand potential vulnerabilities in their critical infrastructure, ensuring they can be fixed before an actual attack occurs.
What OT Penetration Testing (PT) Does?
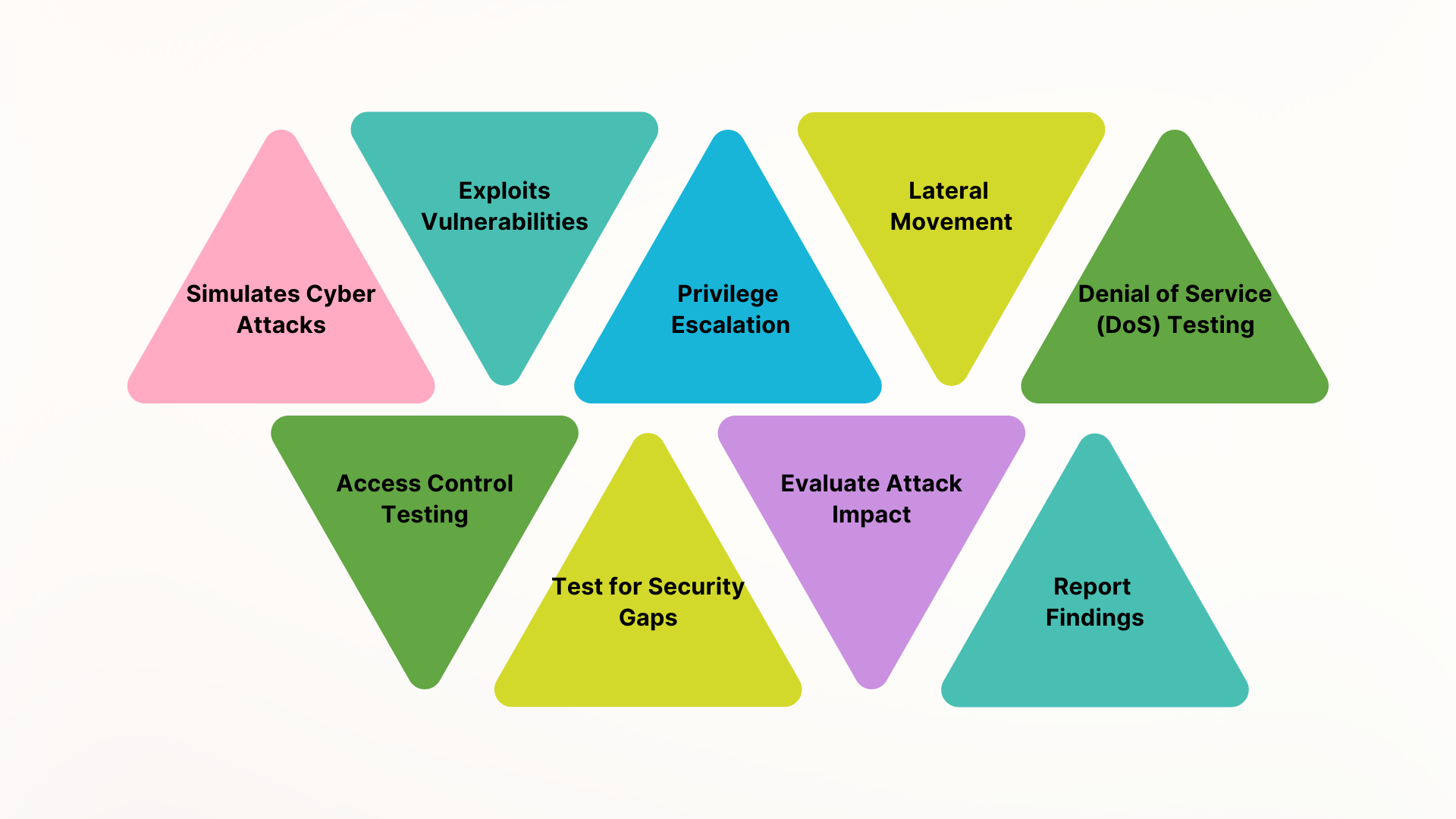
- Simulates Cyber Attacks: Mimics real-world attack scenarios to test system defenses.
- Exploits Vulnerabilities: Attempts to exploit identified weaknesses in OT systems.
- Privilege Escalation: Tests for unauthorized access by escalating privileges within the system.
- Lateral Movement: Checks if attackers can move between OT systems and devices.
- Denial of Service (DoS) Testing: Evaluates system resilience against DoS attacks to ensure availability.
- Access Control Testing: Assesses the effectiveness of security measures like authentication and authorization.
- Test for Security Gaps: Finds hidden vulnerabilities in network, devices, and protocols.
- Evaluate Attack Impact: Analyzes the potential damage of a successful attack on OT systems.
- Report Findings: Provides actionable insights and recommendations based on test results.
OT PT in VAPT helps identify, exploit, and fix security weaknesses in OT environments to prevent real-world cyber threats.
OT VAPT Methodology

-
Pre-Engagement Planning:
- Objective Setting: Define the scope, goals, and assets to be tested.
- Rules of Engagement: Establish guidelines, including testing hours, access permissions, and limitations to ensure ethical testing.
- Asset Discovery: Identify all OT devices, networks, and systems to understand the environment.
-
Information Gathering:
- Network Mapping: Create a map of the OT environment, detailing devices, communication paths, and data flows.
- Vulnerability Scanning: Use automated tools to detect vulnerabilities like outdated software, insecure configurations, and unpatched systems.
- Device Identification: Identify and assess the security of all connected OT devices, including PLCs, sensors, and SCADA systems.
-
Vulnerability Assessment:
- Risk Analysis: Assess and categorize vulnerabilities based on their severity and potential business impact.
- Configuration Review: Examine device configurations for misconfigurations, insecure protocols, and access control weaknesses.
-
Penetration Testing:
- Exploitation Attempts: Simulate cyber-attacks to test how easily vulnerabilities can be exploited, gaining unauthorized access or control.
- Privilege Escalation: Attempt to escalate privileges and gain deeper access to OT systems.
- Lateral Movement: Check if an attacker can move between OT devices and systems, escalating the impact of the breach.
- DoS Testing: Evaluate how OT systems respond to denial-of-service attacks and their ability to maintain availability under stress.
-
Reporting and Analysis:
- Detailed Report: Document vulnerabilities, exploits, and penetration test findings with evidence of risk levels.
- Impact Analysis: Evaluate the business, operational, and financial impacts of vulnerabilities.
- Recommendations: Provide actionable advice on patching vulnerabilities and improving security configurations and policies.
-
Remediation and Retesting:
- Fix Vulnerabilities: Implement fixes such as software patches, configuration changes, and security policy updates.
- Retesting: Test the OT systems again after remediation to ensure vulnerabilities have been resolved and no new issues have emerged.
-
Continuous Monitoring:
- Ongoing Support: Provide continuous monitoring for new vulnerabilities and threats in the OT environment.
- Periodic Reassessment: Conduct regular reassessments to ensure security measures stay up-to-date with emerging threats.
Request free consultation - Click Here
Common Vulnerabilities Found During OT Penetration Testing (OT PT):
- Outdated Firmware and Software: Devices and systems running old, unsupported software that contain known security flaws.
- Weak Authentication Mechanisms: Use of weak passwords, default credentials, or lack of multi-factor authentication for OT devices.
- Insecure Communication Channels: Sensitive data or control commands transmitted over unencrypted or weakly encrypted channels (e.g., plain HTTP instead of HTTPS).
- Uncontrolled Network Access: Lack of proper network segmentation, allowing attackers to move laterally between OT devices and systems.
- Exposed Remote Access: Remote access points with weak or no security controls, such as VPNs without encryption or proper access restrictions.
- Misconfigured Firewalls and Security Devices: Firewalls, IDS/IPS, or other security tools misconfigured, allowing unfiltered traffic or failing to detect threats.
- Lack of Device Authentication: OT devices that don't authenticate each other, allowing unauthorized devices or attackers to interact with the network.
- Vulnerable SCADA and PLC Systems: SCADA (Supervisory Control and Data Acquisition) and PLC (Programmable Logic Controller) systems with known vulnerabilities or poor configurations.
- Physical Access to OT Systems: Insufficient physical security, allowing unauthorized personnel to tamper with OT devices and systems.
- Inconsistent Patch Management: OT systems not regularly patched or updated, leaving them vulnerable to known exploits and threats.
Benefits of OT VAPT by DigiFortex
- Improved Security Posture: OT VAPT identifies potential vulnerabilities and exploits them to improve your security measures. Our testing ensures that your OT systems are secure against cyber-attacks and other threats.
- Minimized Downtime: Identifying and addressing vulnerabilities before they are exploited prevents costly downtime. With DigiFortex OT VAPT services, we ensure your critical OT systems remain operational, reducing the risk of disruption.
- Regulatory Compliance: Our comprehensive testing ensures that your OT systems meet industry regulations and standards. This minimizes the risk of non-compliance penalties and enhances your organization’s credibility in the industry.
- Reduced Risk of Cyber-Attacks: By performing penetration testing and identifying vulnerabilities in your OT environment, we significantly reduce the chances of a cyber-attack. Our services help prevent data breaches, intellectual property theft, and operational failures.
- Enhanced Threat Intelligence: Our OT VAPT services provide valuable threat intelligence, allowing you to stay ahead of emerging threats. We equip your organization with the knowledge to address potential cyber risks proactively.
Request free consultation - Click Here
Why Choose DigiFortex for OT VAPT?
- Certified Experts: CIPPE, CCSA, CCNA, HPOV, DCPLA, CEH, CISSP, CISM, ISO27001 LA.
- ISO 27001:2022 Certified & CERT-In Empanelled: DigiFortex is ISO 27001:2022 certified and CERT-In empanelled for providing information security services. We bring unparalleled expertise to every project.
- Expertise: Our team consists of certified professionals with years of experience in OT security. We leverage the latest tools and techniques to ensure thorough testing and actionable results.
- Customized Approach: We understand that every organization’s OT infrastructure is unique. Our OT VAPT services are tailored to your specific needs, ensuring that we focus on the most critical areas of your OT environment.
- Comprehensive Reports: After testing, we provide detailed reports with clear, actionable recommendations. Our reports help you understand your security posture and the steps needed to secure your OT systems.
- Continuous Support: OT security is an ongoing process. DigiFortex offers ongoing monitoring and maintenance to keep your systems secure as new threats emerge.
Secure Your Critical Infrastructure with DigiFortex
In today’s connected world, Operational technology (OT) systems are vulnerable to evolving cyber threats. DigiFortex’s OT VAPT services provide a proactive approach to identifying and addressing vulnerabilities in your critical infrastructure. By simulating real-world attacks, we help safeguard your OT environment from potential risks, ensuring seamless and secure operations.
Partner with DigiFortex today to strengthen your OT security, mitigate risks, and ensure the resilience of your most essential systems. Stay one step ahead of cyber threats.
Request free consultation - Click Here