🚀 Introduction: A New Quantum Frontier in Cybersecurity
As the world accelerates toward quantum computing breakthroughs, the very fabric of cybersecurity is being rewritten. Traditional encryption methods, network defence models, and even attack detection algorithms will soon face unprecedented challenges.
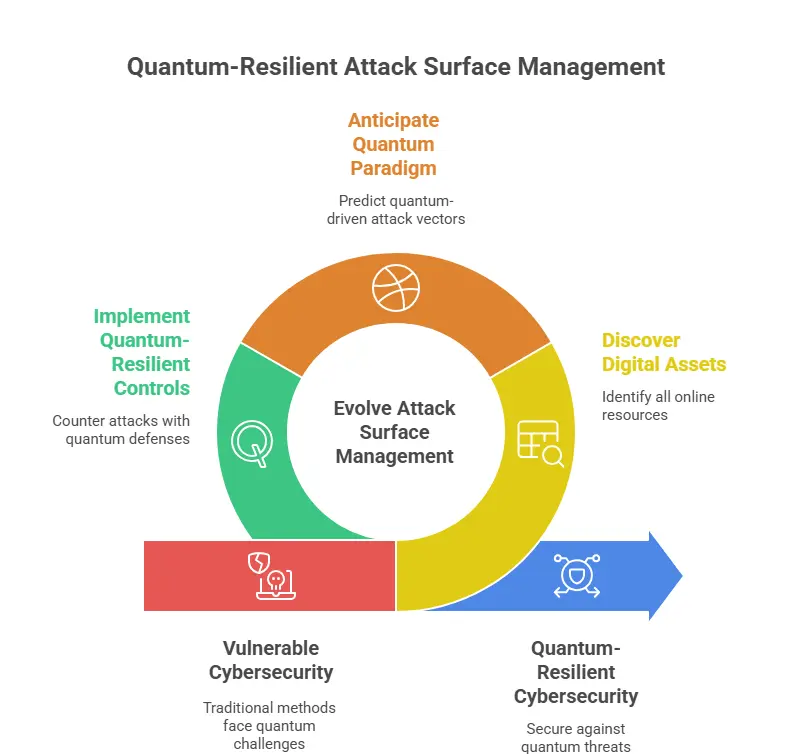
For security leaders, Attack Surface Management (ASM) must now evolve from simply discovering digital assets to anticipating a quantum-driven paradigm, where ttackers may exploit quantum algorithms and defenders must counter with quantum-resilient controls.
We’re entering the Quantum-Era Attack Surface — where every bit, qubit, and key counts.
⚛️ What Makes Quantum Threats Different?
Unlike classical computers, quantum machines process data through qubits, enabling them to perform complex computations, such as prime factorization and discrete logarithm calculations at speeds unimaginable today.
This power fundamentally disrupts the foundation of cybersecurity:
- 🔐 Cryptography Vulnerability: RSA, ECC, and many symmetric encryption schemes will become obsolete under algorithms like Shor’s and Grover’s.
- 🌐 Expanded Digital Estate: Quantum-enabled networks, QKD (Quantum Key Distribution) systems, and hybrid quantum classical infrastructures will introduce new asset types and communication surfaces.
- 🧠 Quantum-AI Synergy: The fusion of quantum computing and AI may generate autonomous, adaptive attack models capable of bypassing static defence mechanisms.
In short, the attack surface itself becomes quantum faster, smarter, and less predictable.
🧭 The Quantum Attack Surface: What Changes?
In the quantum era, Attack Surface Management must account for five critical domains of exposure:
| Domain | Quantum-Era Exposure Example | ASM Focus Area |
|---|---|---|
| Cryptographic Assets | Outdated RSA/ECC certificates, weak key management, long-lived keys vulnerable to store-now-decrypt-later attacks; hardcoded secrets. | Crypto-asset discovery & inventory; key lifecycle tracking; automated alerts for long-lived or weak keys; PQC migration prioritisation. |
| Data-in-Transit Channels | Classical-quantum hybrid communication paths (QKD gateways), mixed TLS/QKD tunnels, misconfigured quantum gateways and fallback channels. | Continuous channel visibility & integrity checks; certificate & channel lifecycle monitoring; automated validation of QKD links. |
| AI/ML Pipelines | Quantum-enhanced adversarial attacks, model inversion using quantum sampling, poisoned training datasets, and exposed model endpoints. | Integrate model & dataset discovery into ASM; provenance checks for ML artifacts; runtime telemetry for model endpoints; adversarial testing. |
| Supply Chain & APIs | Quantum SDKs/APIs and third-party QaaS (Quantum-as-a-Service) dependencies; compromised toolchains and unsigned artifacts. | Vendor dependency mapping; SBOM & artifact signature verification; continuous scanning for vulnerable/unsigned quantum components. |
| IoT / OT Ecosystems | Edge systems connecting to quantum simulators or quantum sensors, legacy OT devices with weak crypto, and time-synchronisation channels. | Endpoint telemetry ingestion; attack-path simulation across OT/IT; segmentation validation; patch posture & mitigation playbooks. |
DigiFortex research shows that organizations embracing post-quantum readiness early gain up to 40% higher resilience against emerging threat vectors compared to those still using static ASM practices.
🔭 Quantum-Enabled Attack Scenarios (2026-2030)
To visualize the shift, here are realistic scenarios that will dominate by 2026-2027:
- 🧮 Scenario 1: Crypto-Harvesting for “Store-Now-Decrypt-Later” Attacks – Adversaries collect encrypted data today, intending to decrypt it once quantum computing matures. ASM platforms must flag long-lifetime encryption keys and unpatched SSL/TLS endpoints now, before they become time bombs.
- 🕵️♂️ Scenario 2: Quantum-Powered Lateral Movement – Quantum-AI models may map network paths and predict vulnerabilities faster than traditional reconnaissance. ASM must incorporate behavioural modelling and predictive risk scoring to stay ahead.
- ⚙️ Scenario 3: Compromised Quantum APIs – As organizations adopt quantum development kits and APIs, compromised or backdoored SDKs could serve as entry points into sensitive systems. ASM must extend API inventorying and digital signature verification into the quantum domain.
🧩 Preparing ASM for Quantum-Era Defence
- ✅ Quantum-Resilient Cryptography Inventory - Begin by mapping every cryptographic instance across your digital estate certificates, keys, encryption protocols, and TLS configurations. Classify them by quantum vulnerability level.
- ✅ Integrate Post-Quantum Algorithms (PQAs) - Transition toward algorithms endorsed by NIST’s Post-Quantum Cryptography Standardization Project. e.g., CRYSTALS-Kyber and Dilithium. Your ASM framework should flag assets that haven’t yet migrated.
- ✅ Simulate Quantum-Driven Attack Paths - Use advanced ASM platforms capable of attack-path simulation not just scanning. Simulate how a quantum adversary might chain together exposures using AI-enhanced reconnaissance.
- ✅ Secure Quantum Communication Channels - If your infrastructure involves QKD or quantum cloud services, ASM must continuously validate channel integrity, endpoint configuration, and encryption lifecycle.
- ✅ Integrate ASM with Governance & Compliance Frameworks - Ensure ASM data aligns with ISO 27001:2022 control objectives and CERT-In advisories. By embedding ASM findings into your GRC stack, you strengthen both security assurance and regulatory confidence.
🛡️DigiFortex Perspective: Building Quantum-Ready Visibility
At DigiFortex, our vision of next-generation ASM goes beyond discovery — it’s about prediction and resilience.
Our certified experts (CISSP, CIPP/E, CISA, CISM, CEH, ISO 27001 LA, DCPLA) are already integrating quantum-risk simulation, AI-driven threat modelling, and LLM-based predictive analytics into our ASM frameworks.
By combining continuous exposure management with quantum-aware analysis, we help enterprises:
- Discover hidden, hybrid, and quantum-linked assets.
- Prioritize crypto-vulnerable and high-impact nodes.
- Transition toward post-quantum cryptography maturity.
- Build quantum-resilient digital ecosystems across cloud, IoT, and OT environments.
🌐 The Road Ahead: From Reactive to Predictive ASM
Between 2026 – 2027, ASM will no longer be about what’s visible today — but about what could be exploited tomorrow.
Quantum computing will redefine both the speed and scope of cyber conflict.
Organizations that wait will react; those who prepare will predict.
The Quantum-Era Attack Surface demands proactive governance, AI-driven insight, and quantum-safe adaptation.
✳️ Final Thought
The post-quantum world won’t just test our cryptographic systems it will test our preparedness, adaptability, and foresight.
By embracing Quantum-Aware Attack Surface Management, enterprises can future-proof their defences and stay resilient in an era where computation itself becomes the ultimate weapon.
👉 DigiFortex empowers organizations to secure their quantum future through advanced ASM, AI-driven analytics, and PQC readiness frameworks.
To know more: Click Here

DigiFortex is a Cyber Security company focused on enhancing Security, Governance, Risk, Compliance (GRC) and Privacy postures for enterprises. Our flagship offerings are GRC, Advanced Penetration Testing(VA/PT), Cloud Security (CNAPP), Next-Gen Security Operation Center(SOC), MSSP, v-CISO and products for advanced Security Assessments.
-
Get in Touch
© 2025 DigiFortex. All Rights Reserved.