The Psychology of Cyber Attacks: What Red Teams Know About Human Behavior That Tools Don’t
Cybersecurity frameworks, tools, and compliance programs continue to evolve, yet the most successful cyberattacks still bypass technology and exploit people. This is the dimension that Red Teams understand better than any automated system: cyberattacks are psychological operations disguised as technical intrusions. Attackers do not simply exploit vulnerabilities—they exploit cognitive biases, decision patterns, emotional triggers, and organisational behaviour. In this sense, the human mind is not just a vulnerability; it is the primary attack surface. Red Team assessments reveal these invisible weaknesses that traditional VAPT, cloud hardening, or SOC monitoring cannot detect alone.
How Attackers Influence Human Decision-Making
Skilled attackers craft their strategies around predictable human tendencies. Red Teams emulate these tactics to uncover how employees react under real-world conditions. Some of the most exploited psychological levers include:
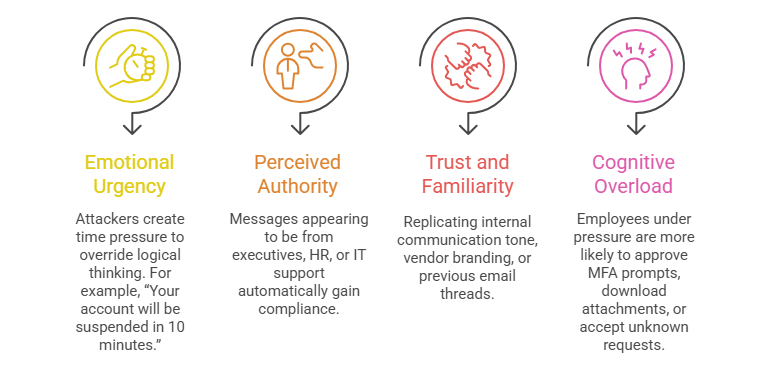
Understanding these patterns is critical because technology cannot filter human instinct, but Red Teams can simulate it.
Common Psychological Attack Techniques Used by Adversaries
| Psychological Lever | Attackers’ Use Case | Typical Scenario |
|---|---|---|
| Urgency Bias | Reduces decision time, increases errors | “Invoice overdue — process immediately” |
| Authority Bias | Exploits hierarchical obedience | CEO or CFO impersonation request |
| Familiarity Bias | Makes malicious communication appear normal | Cloned vendor pdf or email thread |
| Reward Bias | Employees respond positively to incentives | “You are eligible for expense reimbursement” |
| Fear/Threat Bias | Forces rapid compliance | “Email storage full — verify to avoid lockout” |
These psychological models form the foundation of modern cybercrime, and Red Teams replicate them to test organisational resilience.
Why Technology Alone Fails Against Human-Centric Attacks
Despite major investments in SOC platforms, SIEM correlation, IAM, and endpoint protection, one factor remains outside the visibility of all automated security controls: the emotional and cognitive state of the user. Cybersecurity tools detect anomalies, but they cannot detect hesitation, trust, stress, or the subtle pressure employees feel during a normal workday. Red Teams expose these gaps by observing:
- How employees verify requests,
- How departments communicate under urgency,
- How decisions change during high workload periods,
- And how attackers could influence these moments.
This integrated human analysis is where Red Teams provide insight that no scanner, dashboard, or AI model can replicate—and why they play a critical role alongside traditional VAPT and v-CISO programs.
Human Factors Red Teams Uncover That Tools Cannot
Red Teams evaluate people, culture, and process—not just systems. They frequently identify human-driven weaknesses such as:
- Unverified Internal Requests: Employees assume internal emails are automatically legitimate.
- Inconsistent Approval Practices: MFA fatigue or rushed approvals during peak work hours.
- Gaps in Cross-Department Communication: Finance, HR, and IT often do not verify instructions with each other.
- Security Bypass Habits: Employees working around controls for speed or convenience.
- Process Blind Spots: Missing escalations, unclear ownership, or outdated procedures exploited by attackers.
These insights enable v-CISOs and SOC teams to redesign workflows, reduce human error, and strengthen real-world resilience beyond technical patching.
Key Human-Centric Weaknesses Found During Red Team Engagements
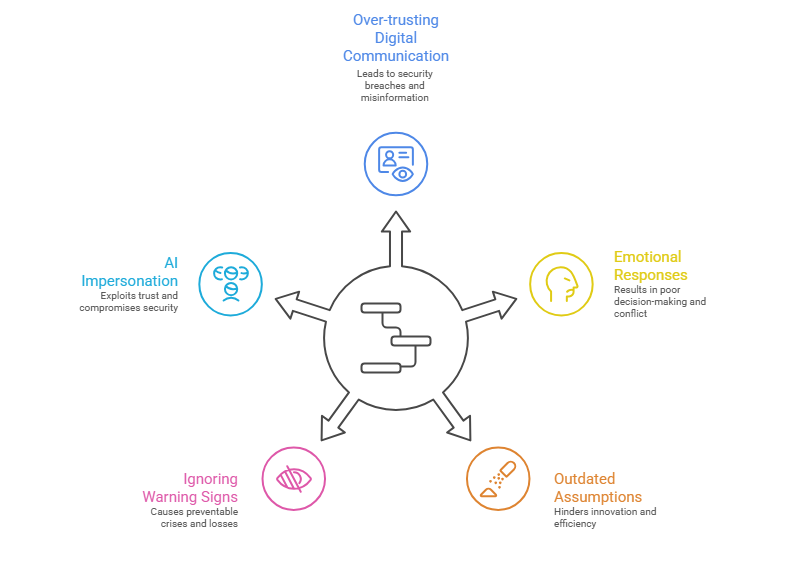
These are not flaws in technology—they are natural human tendencies. But in cybersecurity, they provide attackers with a direct path inside the organisation.
Conclusion
Cybersecurity is not only a technical discipline—it is a psychological battlefield. Modern attackers rely on behavioral manipulation far more than technical skill. Red Teams bring this reality to the forefront by exploring the human layer: how employees think, react, trust, follow authority, and make decisions under pressure. When combined with stronger VAPT programs, v-CISO strategy, SOC monitoring, cloud security hygiene, and tailored security awareness, organisations and MSME in particular, could finally address the one threat surface attackers rely on most: the human mind.
To know more: Click Here

DigiFortex is a Cyber Security company focused on enhancing Security, Governance, Risk, Compliance (GRC) and Privacy postures for enterprises. Our flagship offerings are GRC, Advanced Penetration Testing(VA/PT), Cloud Security (CNAPP), Next-Gen Security Operation Center(SOC), MSSP, v-CISO and products for advanced Security Assessments.
-
Get in Touch
© 2025 DigiFortex. All Rights Reserved.