Inside the Dark Web: How Corporate Data Is Bought, Sold, and Exploited
In 2025, cybercrime is no longer a scattered activity carried out by lone hackers. It has matured into a full-fledged underground economy, with the Dark Web acting as its global marketplace. This hidden side of the internet operates silently but powerfully, where digital identities, company secrets, and customer data are bought and sold like products on an e-commerce site.
Every week in 2025, dozens of new CVEs are being disclosed. Some are low-risk, but others are critical flaws in popular software, systems, or devices you use every day — from firewalls and VPNs to Exchange servers and web apps.
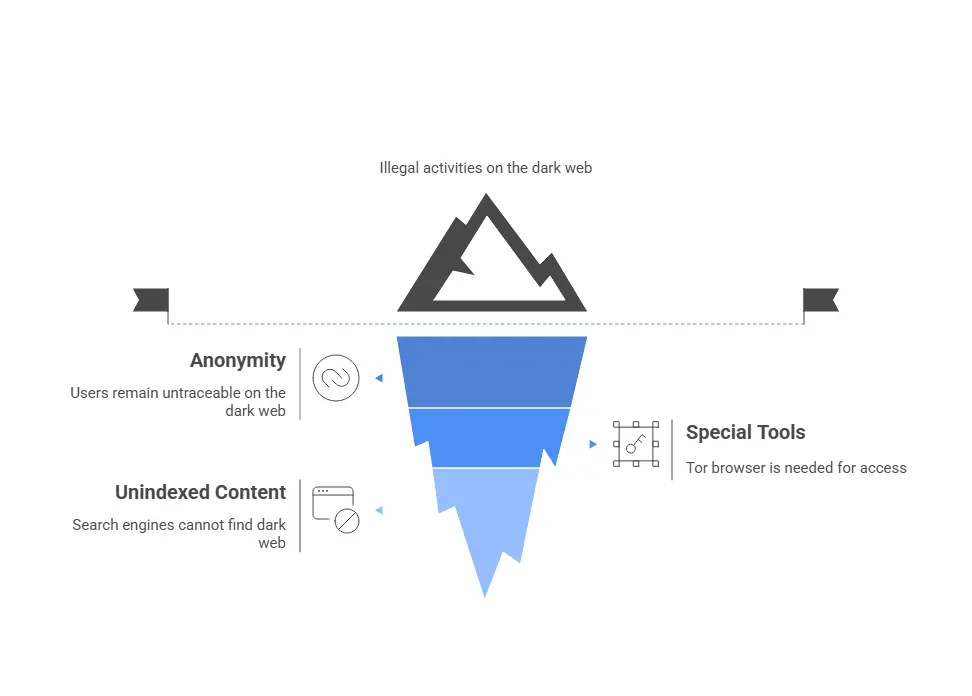
What makes the Dark Web so dangerous is that it operates beyond the reach of regular search engines. You can’t just “Google” what’s happening there. It requires special browsers like Tor to access, and users remain anonymous, making it a safe haven for illegal activities. It’s here that stolen corporate data often ends up, putting businesses at risk of massive losses without them even realizing it.
🔍 What Is the Dark Web?
The Dark Web is a part of the internet that isn’t indexed by Google or other search engines. It requires special tools like Tor browser to access, and it's often used by criminals to stay anonymous.
While not everything on the Dark Web is illegal, it has become a hotbed for cybercrime, including the sale of: Stolen corporate data, Hacked email accounts and passwords, Confidential files, financial records, and source code, Access to internal company systems, Ransomware as a Service tools.
How Does Corporate Data Reach the Dark Web?
🎭 Step 1: Infiltration – How Hackers Break In
In 2025, cybercriminals don’t always need to break down doors. They simply trick people into opening them. Most corporate data breaches start with social engineering—carefully crafted phishing emails, fake login pages, or messages that look like they’re from a trusted colleague or service.
Once the attacker gets access—maybe to a single email account or a poorly secured application—they begin to move quietly, exploring the company’s digital systems like a burglar sneaking through dark hallways. They look for passwords saved in emails, admin panels left unguarded, cloud storage full of sensitive documents, and database backups sitting wide open.
And they don’t rush.
Hackers might stay hidden for days or even weeks, collecting everything from employee logins and customer details to financial reports, internal chat messages, and source code.
🧳 Step 2: Packaging the Data – Turning Secrets into Products
Once they’ve collected enough, the attacker begins to organize the stolen data like a product catalog. They group credentials into neat files, categorize databases by industry, and highlight what’s valuable: “Banking login access,” “Verified emails with passwords,” or “Admin panel access to ecommerce site.”
It’s like preparing goods for a black-market showroom. And that showroom is the Dark Web.
🌐 Step 3: Listing It for Sale – Welcome to the Underground Market
Now comes the shocking part—how professional the Dark Web has become in 2025.
Cybercriminals don’t just dump data randomly. They post it on hidden marketplaces with product images (screenshots of access panels), full descriptions, pricing, and even customer reviews. Think of Amazon or Flipkart—but instead of electronics and clothes, it’s hacked data and login credentials.
Want access to a retail company’s admin panel? ₹20,000 in crypto, A database of 1 lakh Indian banking customers? ₹50,000 and it’s yours, Verified corporate emails with working passwords? Sold per 100 entries.
Payments are made using cryptocurrencies like Bitcoin or Monero, which make the buyers and sellers untraceable. And the sellers? Many offer tech support and “guarantees”—if a password doesn’t work, you can sometimes get a refund.
Yes, the Dark Web is that organized now.
💣 Step 4: The Aftermath – What Happens to Your Data?
Once your data is sold, it begins a new journey—often leading to more attacks. A buyer might:
- Use leaked email credentials to impersonate your CEO and trick employees or clients.
- Install ransomware on your servers and lock your systems for ransom.
- Sell your data again to identity thieves, fraudsters, or even competitors.
- Publish your source code online, destroying your competitive advantage.
And here’s the terrifying part: Most companies don’t know they’ve been breached until they see their data leaked online or are contacted by attackers demanding money.
Real-World Consequences for Businesses
The results of such underground activity can be devastating. Many companies first discover they've been compromised only after their data appears in a leak report or when they're contacted for ransom. By that time, their customer trust is gone, regulatory penalties are looming, and brand reputation is severely damaged.
In India, with the Digital Personal Data Protection (DPDP) Act now in effect, data breaches can also lead to heavy fines if organizations fail to protect user data adequately. The impact is no longer just technical—it’s legal and financial too.
Can You Detect If Your Data Is on the Dark Web?
Yes—but not without expert help. Unlike surface web searches, identifying whether your company’s data is on the Dark Web requires continuous monitoring by cybersecurity professionals. They scan hidden marketplaces, hacker forums, and leaked databases to detect if your credentials or internal files have been exposed.
Many businesses are now investing in Dark Web monitoring tools or partnering with cybersecurity firms to receive alerts in real time. This early detection allows companies to act quickly—resetting passwords, shutting down compromised systems, or alerting customers—before major damage is done.
🛡️ How DigiFortex Helps You Stay Out of the Dark Web
At DigiFortex, we’ve seen firsthand how unpatched vulnerabilities and misconfigurations become the open doors that hackers exploit. That’s why our Vulnerability Assessment and Penetration Testing ( VAPT ) services are built to simulate real-world attacks—before attackers do.
With advanced tools and certified ethical hackers, we identify vulnerabilities across your network, cloud, web applications, mobile apps, LLMs, and more. We simulate the attack paths that real hackers might take, provide actionable remediation strategies, and help ensure compliance with data protection standards. When needed, we also monitor dark web activity for signs of compromised credentials or leaked data related to your organization.
Our goal is simple: Prevent your business from becoming the next listing on a hacker’s marketplace
Be Proactive, Not Reactive
The Dark Web is growing more powerful with every passing year, and in 2025, it’s not just a threat for large corporations—startups, SMEs, and even public sector organizations are being targeted. Cybercriminals don’t care about the size of your business. They care about how easy it is to break in, steal, and sell.
Understanding how the Dark Web operates is the first step. The second is being proactive about cybersecurity. With the right tools, regular assessments, and expert guidance, businesses can reduce their risks and avoid becoming the next victim in this invisible economy.
To know more: Click Here

DigiFortex is a Cyber Security company focused on enhancing Security, Governance, Risk, Compliance (GRC) and Privacy postures for enterprises. Our flagship offerings are GRC, Advanced Penetration Testing(VA/PT), Cloud Security (CNAPP), Next-Gen Security Operation Center(SOC), MSSP, v-CISO and products for advanced Security Assessments.
-
Get in Touch
© 2025 DigiFortex. All Rights Reserved.