Introduction: Why CVEs Are Your Silent Security Threat
In today’s cybersecurity landscape, the biggest breaches often don’t come from advanced, unknown hacking techniques. They come from known vulnerabilities — those already documented in public databases like the CVE (Common Vulnerabilities and Exposures) list.
Every week in 2025, dozens of new CVEs are being disclosed. Some are low-risk, but others are critical flaws in popular software, systems, or devices you use every day — from firewalls and VPNs to Exchange servers and web apps.
Vulnerability Assessment and Penetration Testing (VAPT) helps organizations identify if these vulnerabilities exist inside their environment, how they can be exploited, and what the impact could be if attackers got there first.
What Is a CVE and Why Is It Dangerous?
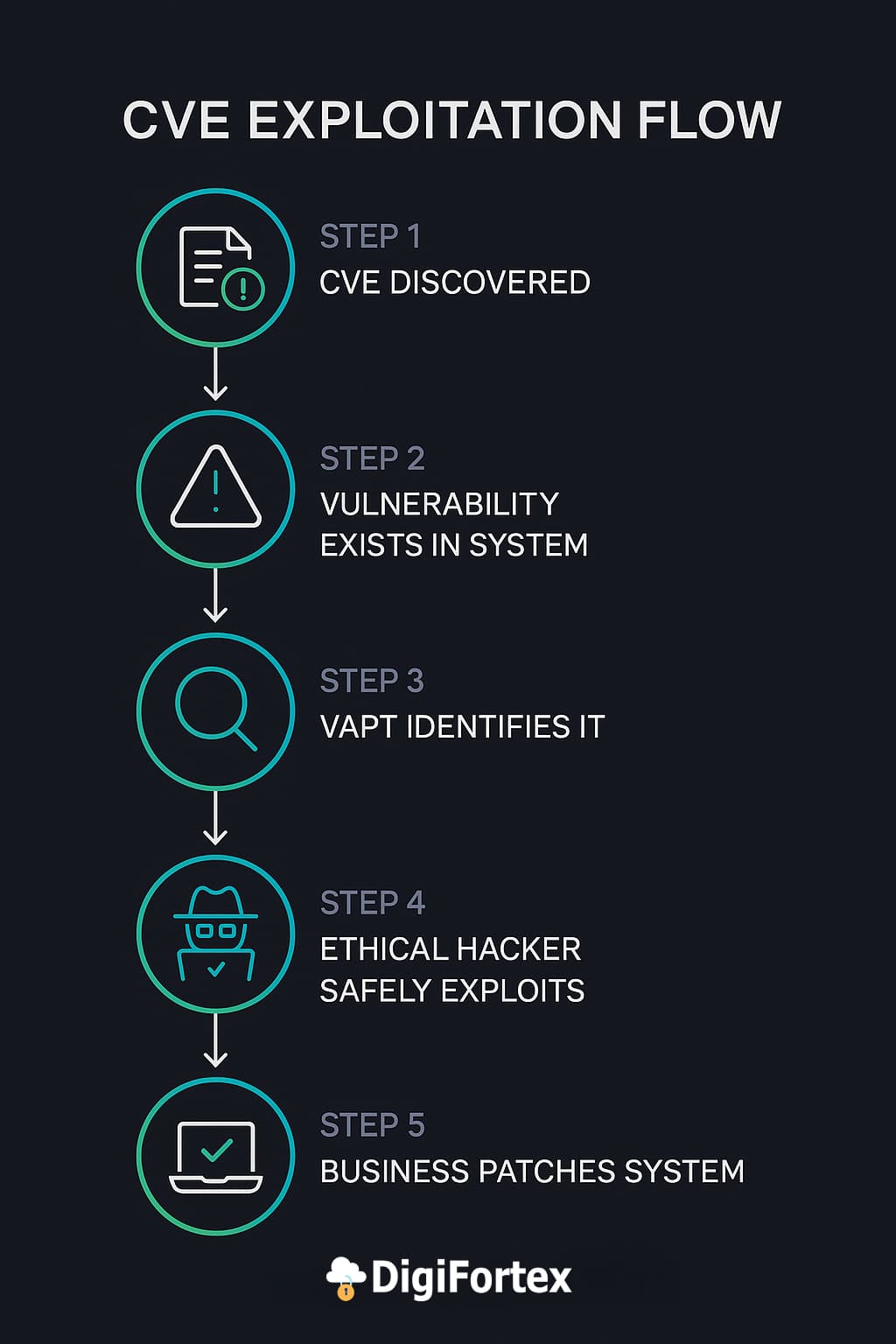
Each CVE represents a specific, publicly known vulnerability. Think of it like an entry in a hacker’s to-do list. When a CVE is published, attackers often start scanning the internet within hours to find systems that haven’t patched it yet.
The real problem? Many organizations don’t know which CVEs affect them until it’s too late — or they assume automatic patching will handle it. That’s where VAPT helps, by actively simulating how attackers exploit these vulnerabilities in your own systems.
Top Real CVE Exploits in 2025 and What We Learned
- CVE-2025-12543: FortiGate VPN RCE
- Used in real-world attacks to take over government networks
- Exploitable without even logging in — extremely dangerous
- Found in VAPT projects during external infrastructure testing
- CVE-2025-09012: Microsoft Exchange Privilege Escalation
- Allows a low-level user to become an admin
- Often part of attack chains — phishing + privilege escalation + data exfiltration
- Identified in simulated phishing + VAPT tests for BFSI clients
- CVE-2025-15789: Apache Struts OGNL Injection
- Same family of vulnerability as the Equifax breach (2017)
- Can be triggered by sending crafted HTTP requests
- Common in outdated e-commerce and logistics websites
- They don’t always know what’s running were
- They miss dependencies (e.g., web servers with outdated libraries)
- They may patch the system but not the application
- Attackers use automated scanners to find unpatched systems within hours of a CVE release.
- Which CVEs exist in your environment
- Whether those CVEs are actually exploitable right now
- What would happen if they were exploited
- What specific steps you need to take to fix or mitigate them.
This Teaches VPNs are supposed to protect your network. But if the VPN appliance itself is vulnerable, then you're trusting a weak lock on your front door
This Teaches It’s not enough to patch your systems once. New CVEs are weaponized into multi-stage attacks. VAPT shows how attackers chain these flaws.
This Teaches Public-facing web apps must be scanned AND manually tested regularly. One legacy plugin or unpatched library can become your weakest link.
Why Just Patching Isn’t Enough
Many companies apply patches based on vendor newsletters or update schedules — but:
VAPT helps verify if your patches are effective or if the vulnerability is still open due to a misconfiguration.
How VAPT Helps You Handle CVEs the Right Way
VAPT doesn’t just scan for vulnerabilities. It mimics how real hackers think. Security teams match discovered system weaknesses with CVEs and then attempt to exploit them — not to break the system, but to show you how easy it would be for someone else to do it maliciously.
The advantage of VAPT is that it goes beyond tools and reports. It connects the dots:
Instead of waiting for a red alert from your SIEM or news of a breach in your industry, VAPT tells you now where you’re most exposed and helps you act before the damage is done.
Who Should Be Worried About CVEs?
Every organization using software, hardware, or cloud infrastructure is exposed to CVEs. However, attackers tend to focus on industries where the impact is the highest.
If you’re in banking or finance, attackers are actively exploiting vulnerabilities in email systems, multi-factor authentication flows, and VPNs. In ecommerce, they go after outdated web apps, payment gateways, and forgotten APIs. Healthcare organizations face risks through connected medical devices and legacy platforms, while manufacturing firms are vulnerable through OT and SCADA systems.
In each of these sectors, the same pattern is visible — attackers use public CVEs, combine them with phishing or misconfigurations, and execute powerful breaches that go undetected until it’s too late.
Why Patching Alone Isn’t Enough
Most organizations believe they are safe once a vendor releases a patch. But here’s the truth: patches don’t automatically fix vulnerabilities. Misconfigurations, outdated backups, dependencies, and even simple delays in applying patches leave CVEs wide open.
That’s why VAPT is critical. It doesn’t just check if a patch exists — it checks if the vulnerability is still exploitable in your actual system setup.
Final Thoughts
Cybersecurity in 2025 is not just about reacting to attacks — it’s about anticipating them. With thousands of CVEs being published every month, your organization needs to go beyond checklists and vulnerability scans.
VAPT turns passive knowledge into active defence. It takes the latest CVE information, tests your systems in real-world conditions, and gives you a clear roadmap to close gaps — before someone else takes advantage of them.
If you haven’t done a CVE-focused VAPT in the last 3–6 months, now is the time. DigiFortex’s expert team monitors the latest critical vulnerabilities daily, aligns them with your technology stack, and performs deep assessments to expose what attackers could find — and stop them before they do.
To know more: Click Here
