APT – The Cyberattack You Won’t Even Notice
Most cyberattacks shout for attention—your screen freezes, files get locked, or pop-ups appear. But APT attacks (Advanced Persistent Threats) work differently. They’re like spies—quiet, focused, and deadly. Their goal is not to destroy. It’s to stay hidden, steal valuable data, and leave silently.
This blog walks you through story of an APT attack on a pharma company to show how these attacks unfold and how your organization can defend against them.
📧 The Infiltration Begins
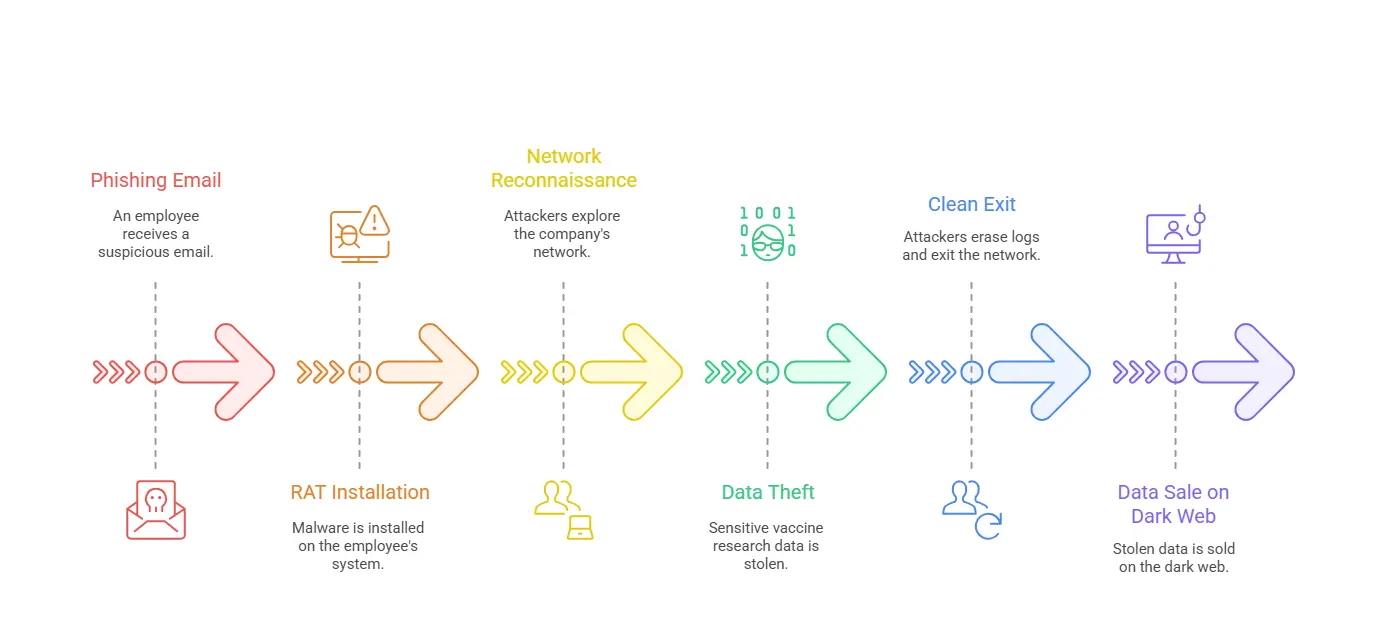
It all began with a phishing email.
A mid-level employee received an email that looked like it came from their HR team. It was titled “Internal COVID-19 Policy – Urgent Action Needed” with an attachment. Trusting the source, they clicked.
In that one click, a Remote Access Trojan (RAT) was installed on their system.
The malware opened a backdoor for the attackers—allowing them to remotely control the system. But there were no visible signs. Everything looked normal.
💡 What makes APTs dangerous?
They don’t crash your system or alert antivirus software. They sneak in and quietly observe.
👁️🗨️ The Observation Phase
The APT group didn't rush. For 4 weeks, they watched.
Using the infected system, they began network reconnaissance—exploring how the company's network was structured:
- Who had admin access?
- Where were sensitive files stored?
- What internal tools were used?
They installed keyloggers to capture usernames and passwords. They cracked credentials, moved laterally across the network, and gathered intelligence without making noise.
🎯 The Mission: Steal Vaccine Research
The attackers finally found what they were looking for—files related to vaccine development and clinical trial data.
They didn’t copy everything at once (that would look suspicious). Instead, they:
- Split files into small encrypted parts
- Sent them out through normal-looking network traffic
- Scheduled it during working hours to avoid alerts
💡 Why didn’t anyone notice?
Because they mimicked regular employee behaviour, even copying data at peak office times.
👋 The Clean Exit
After almost 90 days inside the system, the hackers had what they came for.
They erased their logs, removed malware, and exited the network cleanly. No alarms were triggered. IT teams didn’t even realize they had been hacked.
Weeks later, a government cybersecurity agency warned the company: “Your confidential data is being sold on the dark web.”
🤖 Who Was Behind This APT?
Investigation revealed the attack came from an APT group backed by a foreign government, likely interested in stealing vaccine research for national advantage.
APT groups are usually Highly skilled, Well-funded, State-sponsored or politically motivated, Focused on espionage, intellectual property theft, and surveillance
They are not interested in quick money or ransomware. Their target is long-term gain through hidden data theft.
🛡️ How to Protect Against APT Attacks
Defending against APTs is tough—but not impossible. Here’s what you can do:
- 🔐 Employee Awareness Training Phishing is still the way APTs enter. Educate employees to recognize suspicious emails and attachments.
- 🧱 Zero Trust Security Don’t automatically trust internal traffic. Use Zero Trust Architecture to validate every user and device.
- 👀 Threat Detection Tools Use Endpoint Detection & Response (EDR) and Security Information and Event Management (SIEM) to spot unusual behaviour.
- 🧪 Regular VA/PT Audits Run Vulnerability Assessment and Penetration Testing (VA-PT) regularly to discover weak points before attackers do.
- 🌐 Network Segmentation Divide your internal network so that if one part is compromised, attackers can’t access everything.
🧠 Final Thoughts: Don’t Wait for a Wake-Up Call
APT attacks are real. They don’t just happen in movies or government organizations. Private companies, especially in sectors like healthcare, energy, defence, and finance, are high-value targets too.
You may not know it, but someone could already be watching your network silently.
At DigiFortex, we’ve helped organizations detect, respond, and recover from APTs with advanced threat hunting.
To know more: Click Here
DigiFortex is a Cyber Security company focused on enhancing Security, Governance, Risk, Compliance (GRC) and Privacy postures for enterprises. Our flagship offerings are GRC, Advanced Penetration Testing(VA/PT), Cloud Security (CNAPP), Next-Gen Security Operation Center(SOC), MSSP, v-CISO and products for advanced Security Assessments.
-
Get in Touch
© 2025 DigiFortex. All Rights Reserved.