Understanding India’s DPDP — What the New Rules Mean for Businesses & Individuals
In November 2025, India crossed a major milestone: the government officially notified the DPDP Rules, transforming the high-level legal framework of the DPDP Act into an actionable, enforceable set of obligations....
Read MoreThe Psychology of Cyber Attacks
Cybersecurity frameworks, tools, and compliance programs continue to evolve, yet the most successful cyberattacks still bypass technology and exploit people. This is the dimension that Red Teams understand better than any automated system...
Read MoreInside the Attack Surface Management (ASM):
Cyber threats evolve at machine speed. Vulnerabilities emerge faster than patch cycles, and threat actors exploit misconfigurations, forgotten assets, and exposed credentials long before they appear on conventional scanners. ....
Read MoreMSME Playbook: Empowering Smart, Secure, and Resilient Digital Growth
Modern MSMEs operate in a digital economy where attack surfaces multiply faster than defences With interconnected systems, cloud-native workflows, and third-party integrations, the boundaries between “internal” and “external” are blurred ....
Read MoreThe Quantum Attack Surface: Are You Ready for What’s Coming?
Unlike classical computers, quantum machines process data through qubits, enabling them to perform complex computations, such as prime factorization and discrete logarithm calculations at speeds unimaginable today....
Read MoreBeyond Compliance: Building Trust Through Third-Party Risk Management
TPRM is the structured process of identifying, assessing, controlling, and monitoring risks that arise from working with external vendors and partners. These risks are not only technical but also legal, operational, reputational, and regulatory...
Read MoreRBI’s AI Framework: Balancing Innovation with Trust in India’s Financial Sector
Artificial Intelligence (AI) is no longer a futuristic concept—it is already embedded in the way we bank. From real-time fraud detection and alternative credit scoring to multilingual chatbots and automated compliance, AI is transforming the financial landscape...
Read MoreISO 42001: A Practical Guide to Responsible AI Management
ISO/IEC 42001:2023 has emerged as the first certifiable global standard for AI Management Systems (AIMS). It provides organizations with a structured framework for building, deploying, and monitoring AI systems in a manner that is secure, ethical, transparent, and compliant...
Read MoreThe Four Giants of Data Privacy and How They’re Bracing for the AI Storm
At first glance, these laws look similar consent, transparency, rights to delete data. But beneath the surface, they differ in scope, enforcement muscle, and how they’re preparing for the AI-powered future...
Read More🚨 Deepfake Scams, AI Impersonation & the Next Era of Cyber Fraud — Detecting the Undetectable
Today’s cybercriminals are leveraging AI not just as a tool, but as an identity weapon. Deepfake videos, cloned voices, and AI generated personas are being used to impersonate executives, celebrities, government officials, and even loved ones—to extract money, data, and trust ...
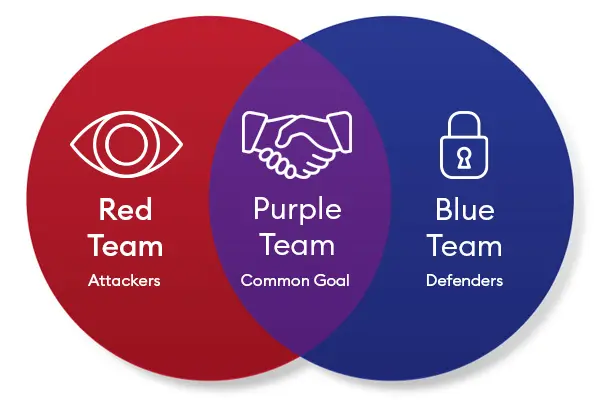
Read MorePurple Teaming: How Red and Blue Teams Work Together to Improve Cyber Resilience
Purple teaming is when Red and Blue Teams join forces—sharing tactics, findings, and techniques—to improve the overall cyber resilience of an organization. Instead of working in silos, they communicate in real time, making security stronger, faster, and smarter...
Read MoreInside the Dark Web: How Corporate Data Is Bought, Sold, and Exploited
In 2025, cybercrime is no longer a scattered activity carried out by lone hackers. It has matured into a full-fledged underground economy, with the Dark Web acting as its global marketplace. This hidden side of the internet operates....
Read MoreAPT Attacks Explained Through a Story of Digital Intrusion
Most cyberattacks shout for attention—your screen freezes, files get locked, or pop-ups appear. But APT attacks work differently.They’re like spies—quiet, focused, and deadly. Their goal is not to destroy. It’s to stay hidden, steal valuable data, and leave silently....
Read MoreFrom Weakness to Breach: VAPT's Latest CVE Discoveries in 2025
In today’s cybersecurity landscape, the biggest breaches often don’t come from advanced, unknown hacking techniques. They come from known vulnerabilities — those already documented in public databases like the CVE (Common Vulnerabilities and Exposures) list....
Read MoreInside the LLM VAPT Process: How Experts Assess and Secure AI Models
Artificial Intelligence is transforming industries at an unprecedented pace. With the rise of powerful tools like ChatGPT, Claude, and other Large Language Models (LLMs), businesses are embracing AI to improve efficiency, customer service, and innovation. But as the use of LLMs grows....
Read MoreSEBI's Latest Cybersecurity Directive: Key Takeaways for Regulated Entities
In today’s digital financial landscape, cyber risks are not just a possibility—they're a certainty. Recognizing this, the Securities and Exchange Board of India (SEBI) has taken a bold step forward with its updated Cybersecurity and Cyber Resilience Framework (CSCRF)....
Read MoreAI-Powered Cyber Attacks: The Next Big Challenge
As artificial intelligence (AI) continues to revolutionize industries, it is also being weaponized by cybercriminals. AI-powered cyber-attacks are rapidly evolving, making traditional security measures obsolete. In 2025, organizations must prepare for a new wave of sophisticated threats...
Read MoreRBI Prepaid Payment Instruments (PPI)
At its core, a Prepaid Payment Instrument is a financial tool that allows individuals to store a certain value of money, which can be used for various transactions. Think of it as a digital wallet or a prepaid card that you load with funds in advance and then use to pay for purchases...
Read MoreRBI Payment Aggregators and Payment Gateway (PAPG) Audit
In the rapidly evolving digital economy, the seamless and secure processing of online transactions is paramount. Central to this ecosystem are Payment Aggregators (PAs) and Payment Gateways (PGs)...
Read MoreSEBI Cyber Security & Cyber Resilience Framework (CSCRF)
In a world where cyber threats evolve every second, organizations need more than just security—they need resilience. SEBI’s Cybersecurity & Cyber Resilience Framework (CSCRF) combines proactive protection with adaptive recovery...
Read MoreHow Long Does It Take To Implement ISO 27001 For Organisations
By Vijay Kumar The timeline for implementing ISO 27001 for the organisations can vary depending on several factors, such as the size of the organization, the scope of the project, and the availability of resources. However, with proper planning and execution, organisations can typically implement ISO 27001 between 6-8 months.
Read MoreThe CFO’s Role In Managing Cybersecurity Threats And Risks
By Vijay Kumar At the World Economic Forum in 2022, Microsoft’s SaCurabitur pulvinar euismod ante, ac sagittis ante posuere ac. Vivamus luctus commodo dolor porta feugiat.tya Nadella said that Russia’s cyber onslaught on Ukraine started 1 year before its special military operation on February 24, 2022. Within days, Ukraine immediately retaliated by hiring hundreds of
Read MoreChilling Cyber Chinks
At the World Economic Forum, Microsoft’s Satya Nadella said Russia’s cyber onslaught on Ukraine started one year before its special military operation on February 24, 2022. While the Russian invasion had a combination of troops, tanks, aircraft and cruise missiles, the first shots were in fact fired hours before when the calendar still said February 23. This attack involved a cyber-weapon called ‘Foxblade’, which was
Read MoreMany Verses Of Metaverse
By Vijay Kumar You can think about this as an embodied internet operated by many different players in a decentralised way. You’re inside of rather than just looking at. We believe that it is going to be the successor to the mobile internet — Mark Zuckerberg, 2021 Euphoric Verse The rapid speed and scale of digitisation has suddenly landed us in a universe,
Read MoreArchitecting Cyber Security
Corona Spiking Cyber Attacks? After having decimated humans and animals internationally, the virulent corona has made inroads across the firewalls, the intrusion detection/prevention systems and the de-militarised zones(DMZ). Don’t get bogged down by these jargons, but the fact is hackers have been super active during the ongoing flu season.
Read MoreOpinion: Smart Strategies For Safe Cloud
Did you ever ponder why there are so many data breaches these days? Did you also notice why such incidents are significantly more on cloud than otherwise? Did you wonder why despite best talents, intents and efforts, businesses get bulldozed besides being publicly embarrassed by a few unknown enemies? Ask any leader and s/he would
Read MoreOpinion: Changing Techscape And Data Privacy
Oh, Not Again!!Whilst you were amidst your deepest slumber or that engaging conversation, have you ever been hounded by calls offering you unsolicited loans, overdraft or balance transfer facilities? Did it stop after you subscribed for DND (Do Not Disturb) registry? Has it become worse that you are now a chronic victim of automated tele-marketing calls
Read MoreLifting Crypto Ban: India Could Be Trendsetter
The lifting of crypto ban is very welcoming given economy is reeling under pressure compounded with the global fear of coronavirus. Cryptocurrency has been more valuable than most top companies despite all the blood bath that has shaken the cryptocurrency in the last 2 years. Cryptocurrency today is more valuable than a Boeing (US$ 162B),
Read More